Setting up a Ldap directory service – step by step.
I’m gonna blog and demonstrate in facts how to configure and administrate a LDAP directory services.
Actually, Ldap is a directory service which informations can be stored as a database and through these ones you may recognize you base authentication. This turns out that you could authenticate an user for multiples services.
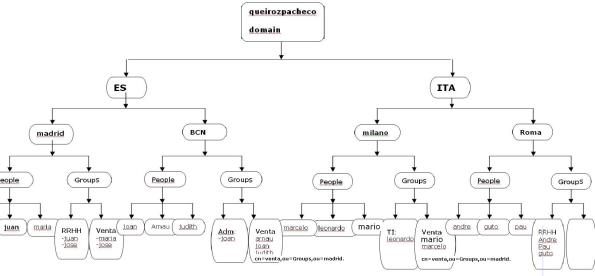
We’re working over the following picture throughout the steps, where it indicates all our ldap tree.
picture1
First of all, we need to install a Linux based on rpm package. I chose a Linux based on it but fell free to install a linux whatever you want.
Once Linux is installed (it’s been installed a CentOS-5), let’s get started.
1- I’d rather to keep a minimal configuration during the installation. After that you can install the package according to you need. This is the point. We’re gonna need to install.
2- Check out if selinux and firewall is disabled so far. We can implement security in another topic.
3- Install the following packages.
-openldap, openldap-clients, openldap-servers
Checking out if selinux and firewall is disabled.
There’re two ways to implement them. The first one is by hand.
Edit /etc/sysconfig/selinux and change the option SELINUX=enforcing to disabled.
Run “chkconfig iptables ip6tables off”
In other way easier is running “system-config-securitylevel-tui” to disable selinux as well as firewall.
Installing openldap.
[root@server01 ~]# yum install openldap openldap-clients openldap-servers
Installed:
openldap-servers.i386 0:2.3.43-3.el5Dependency Installed:
libtool-ltdl.i386 0:1.5.22-6.1Complete!
[root@server01 ~]#
Configuring Ldap server.
1- Run slappasswd and define a password. Copy what comes out from this command already crypt for putting into the following file.
[root@server01 ~]# slappasswd
New password:
Re-enter new password:
{SSHA}Dpksh7aLrhYJulR6gvxH/6rQSinokQqL
[root@server01 ~]#
2- Edit /etc/openldap/slapd.conf and the content has to be like this.
[root@server01 ~]# vi /etc/openldap/slapd.conf
database bdb
suffix “dc=queirozpacheco,dc=com”
rootdn “cn=root,dc=queirozpacheco,dc=com”
rootpw {SSHA}Dpksh7aLrhYJulR6gvxH/6rQSinokQqL
3-Copy DB_CONFIG.example to /var/lib/ldap/DB_CONFIG
[root@server01 ~]# cp /etc/openldap/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
4-Start ldap and make sure that ldap will be started up during the boot.
[root@server01 /]# service ldap start
Checking configuration files for slapd: config file testing succeeded
[ OK ]
Starting slapd: [ OK ]
[root@server01 /]# chkconfig ldap on
[root@server01 /]#
NOTE: Sometimes it’s good for the system to be custom, and I wanna disable some services which aren’t useful so far. If you are using some of them included at the following list just take them out.
for i in acpid atd auditd autofs avahi-daemon bluetooth crond cups firstboot gpm haldaemon hidd ip6tables iptables kudzu pcscd sendmail yum-updatesd; do chkconfig $i off; done
5-These steps following are implemented by hand, you can use migrate scripts which I’ll talk a bit of them later.
1- Define your control domain. All parameters are defined into a file with a ldif extension and imported to ldap base.
[root@server01 ~]# mkdir /var/ldap
[root@server01 ~]# cd /var/ldap/
[root@server01 ldap]# vi base.ldif#base.ldif
dn: dc=queirozpacheco,dc=com
dc: queirozpacheco
objectClass: top
objectClass: domain
2- Import it to ldap base
[root@server01 ldap]# ldapadd -x -W –D ‘cn=root,dc=queirozpacheco,dc=com’ -f base.ldif
Enter LDAP Password:
adding new entry “dc=queirozpacheco,dc=com”[root@server01 ldap]#
3- Define everything else described on the picture1.
Setting countries entries.
[root@server01 ldap]# vi countries.ldif
dn: ou=es,dc=queirozpacheco,dc=com
ou: es
objectClass: top
objectClass: organizationalUnitdn: ou=ita,dc=queirozpacheco,dc=com
ou: ita
objectClass: top
objectClass: organizationalUnit
Adding these entries to ldap base.
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f countries.ldif
Enter LDAP Password:
adding new entry “ou=es,dc=queirozpacheco,dc=com”adding new entry “ou=ita,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
Make sure that it was created successfully:
[root@server01 ldap]# ldapsearch -x -b ‘dc=queirozpacheco,dc=com’ ou=*
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: ou=*
# requesting: ALL
## es, queirozpacheco.com
dn: ou=es,dc=queirozpacheco,dc=com
ou: es
objectClass: top
objectClass: organizationalUnit# ita, queirozpacheco.com
dn: ou=ita,dc=queirozpacheco,dc=com
ou: ita
objectClass: top
objectClass: organizationalUnit# search result
search: 2
result: 0 Success# numResponses: 3
# numEntries: 2
[root@server01 ldap]#
Setting the entries related to “es” organizational Unit.
At beginning, we’ll just create all what we describe for organizational Unit. That means, everything else except users and groups.
Creating es.ldif
[root@server01 ldap]# vi es.ldif
dn: ou=madrid,ou=es,dc=queirozpacheco,dc=com
ou: madrid
objectClass: top
objectClass: organizationalUnitdn: ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com
ou: People
objectClass: top
objectClass: organizationalUnitdn: ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com
ou: Groups
objectClass: top
objectClass: organizationalUnitdn: ou=bcn,ou=es,dc=queirozpacheco,dc=com
ou: bcn
objectClass: top
objectClass: organizationalUnitdn: ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com
ou: People
objectClass: top
objectClass: organizationalUnitdn: ou=Group,ou=bcn,ou=es,dc=queirozpacheco,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
Adding these entries above into ldap database.
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f es.
ldif
Enter LDAP Password:
adding new entry “ou=madrid,ou=es,dc=queirozpacheco,dc=com”adding new entry “ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
adding new entry “ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
adding new entry “ou=bcn,ou=es,dc=queirozpacheco,dc=com”
adding new entry “ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com”
adding new entry “ou=Group,ou=bcn,ou=es,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
Creating ita.ldif
[root@server01 ldap]# vi ita.ldif
dn: ou=milano,ou=ita,dc=queirozpacheco,dc=com
ou: milano
objectClass: top
objectClass: organizationalUnitdn: ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com
ou: People
objectClass: top
objectClass: organizationalUnitdn: ou=Groups,ou=milano,ou=ita,dc=queirozpacheco,dc=com
ou: Groups
objectClass: top
objectClass: organizationalUnitdn: ou=roma,ou=ita,dc=queirozpacheco,dc=com
ou: roma
objectClass: top
objectClass: organizationalUnitdn: ou=People,ou=roma,ou=ita,dc=queirozpacheco,dc=com
ou: People
objectClass: top
objectClass: organizationalUnitdn: ou=Groups,ou=roma,ou=ita,dc=queirozpacheco,dc=com
ou: Groups
objectClass: top
objectClass: organizationalUnit
Adding the entries from ita.ldif to ldap database.
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f ita
.ldif
Enter LDAP Password:
adding new entry “ou=milano,ou=ita,dc=queirozpacheco,dc=com”adding new entry “ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com”
adding new entry “ou=Groups,ou=milano,ou=ita,dc=queirozpacheco,dc=com”
adding new entry “ou=roma,ou=ita,dc=queirozpacheco,dc=com”
adding new entry “ou=People,ou=roma,ou=ita,dc=queirozpacheco,dc=com”
adding new entry “ou=Groups,ou=roma,ou=ita,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
Creating the users and groups and setting the values.
Madrid Users:
[root@server01 ldap]# vi users-madrid.ldif
dn: uid=jose,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com
uid: jose
cn: Jose Martinez
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/jose
uidnumber: 500
gidnumber:500
userpassword: jose123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=juan,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com
uid: juan
cn: Juan Perez
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/juan
uidnumber: 501
gidnumber:501
userpassword: juan123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=maria,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com
uid: maria
cn: Maria Munoz
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/maria
uidnumber: 502
gidnumber:502
userpassword: maria123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7
Adding users-madrid.ldif to ldap database
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f users-madrid.ldif
Enter LDAP Password:adding new entry “uid=jose,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
adding new entry “uid=juan,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
adding new entry “uid=maria,ou=People,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
Setting and creating the groups of Madrid OU.
[root@server01 ldap]# vi madrid-group.ldif
dn: cn=RRHH,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com
cn: RRHH
objectClass: top
objectClass: posixGroup
gidnumber: 503
memberUid: juan
memberUid: josedn: cn=venta,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com
cn: venta
objectClass: top
objectClass: posixGroup
gidnumber: 504
memberUid: maria
memberUid: jose
Adding Madrid-group to ldap database:
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f madrid-group.ldif
Enter LDAP Password:
adding new entry “cn=RRHH,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com”adding new entry “cn=venta,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
Creating Barcelona’s users and group.
Barcelona-users.ldif
[root@server01 ldap]# vi bcn-users.ldif
dn: uid=joan,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com
uid: joan
cn: Joan Monserrat
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/joan
uidnumber: 505
gidnumber:505
userpassword: joan123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=arnau,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com
uid: arnau
cn: Arnau Torres
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/arnau
uidnumber: 506
gidnumber:506
userpassword: arnau123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=judith,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com
uid: judith
cn: Judith da Silva
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/judith
uidnumber: 507
gidnumber:507
userpassword: judith123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7
Adding the entries from bcn-users to ldap database.
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f bcn
-users.ldif
Enter LDAP Password:
adding new entry “uid=joan,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com”adding new entry “uid=arnau,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com”
adding new entry “uid=judith,ou=People,ou=bcn,ou=es,dc=queirozpacheco,dc=com”
Creating groups and assigning their users.
NOTE: there’s a group called “venta” and it’s not allowed to create 2 groups where the names match. Solution: Add into the existent group the users engaged. For doing that, we need using changetype flag as modify.
[root@server01 ldap]# vi bcn-group.ldif
dn: cn=adm,ou=Groups,ou=bcn,ou=es,dc=queirozpacheco,dc=com
cn: adm
objectClass: top
objectClass: posixGroup
gidNumber: 508
memberUid: joandn: cn=venta,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com
changetype: modify
add: memberUid
memberUid: arnau
memberUid: joan
memberUid: judith
Applying these rules above.
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f bcn
-group.ldif
Enter LDAP Password:
adding new entry “cn=adm,ou=Groups,ou=bcn,ou=es,dc=queirozpacheco,dc=com”modifying entry “cn=venta,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com”
Checking out:
[root@server01 ldap]# ldapsearch -x -b ‘dc=queirozpacheco,dc=com’ cn=venta
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: cn=venta
# requesting: ALL
## venta, Groups, madrid, es, queirozpacheco.com
dn: cn=venta,ou=Groups,ou=madrid,ou=es,dc=queirozpacheco,dc=com
cn: venta
objectClass: top
objectClass: posixGroup
gidNumber: 504
memberUid:: bWFyaWEg
memberUid: jose
memberUid: arnau
memberUid: joan
memberUid: judith
So, over there we need creating the same thing to users which belong to ITA Organizational Unit.
Adding milano’s users and groups.
# user-milano.ldif
dn: uid=marcelo,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com
uid: marcelo
cn: Marcelo Tarantela
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/marcelo
uidnumber: 509
gidnumber:509
userpassword: marcelo123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=leonardo,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com
uid: leonardo
cn: Leonardo Formaggi
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/leonardo
uidnumber: 510
gidnumber:510
userpassword: leonardo123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7dn: uid=mario,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com
uid: mario
cn: Mario Bross
objectClass: top
objectClass: posixAccount
objectClass: account
objectClass: shadowAccount
loginshell: /bin/bash
homedirectory: /home/mario
uidnumber: 511
gidnumber:511
userpassword: mario123
shadowLastChange: 11892
shadowMax: 99999
shadowWarning: 7
Applying the user-milano.ldif entries
[root@server01 ldap]# ldapadd -x -W -D ‘cn=root,dc=queirozpacheco,dc=com’ -f use
rs-milano.ldif
Enter LDAP Password:
adding new entry “uid=marcelo,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=co
m”adding new entry “uid=leonardo,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=c
om”adding new entry “uid=mario,ou=People,ou=milano,ou=ita,dc=queirozpacheco,dc=com”
[root@server01 ldap]#
So, you need to apply all those instructions what we’ve applied before.
After that, we need to set the ldap client and create the home’s users directory.
Run authconfig-tui or edit /etc/nsswitch.conf and /etc/openldap/ldap.conf and /etc/ldap.conf
[root@server01 etc]# vi /etc/nsswitch.conf
passwd: files ldap
shadow: files ldap
group: files ldap
automount: files ldap[root@server01 etc]# vi /etc/ldap.conf
uri ldap://192.168.1.2
ssl no
tls_cacertdir /etc/openldap/cacerts
pam_password md5[root@server01 openldap]# vi /etc/openldap/ldap.conf
BASE dc=queirozpacheco,dc=com
URI ldap://192.168.1.2[root@server01 home]# mkdir /home/jose; chown jose /home/jose
[root@server01 home]# mkdir /home/juan; chown juan /home/juan
[root@server01 home]# mkdir /home/maria; chown maria /home/maria
[root@server01 home]# mkdir /home/joan; chown joan /home/joan
[root@server01 home]# mkdir /home/arnau; chown arnau /home/arnau
[root@server01 home]# mkdir /home/judith; chown judith /home/judith
Now, try to log in with some of these users created in ldap database.
bash-3.2$ pwd
/home/joan
bash-3.2$ whoami
joan
bash-3.2$
It works!!!
Cheers form Carlos.
Great work
thanks very much!